Evil Eye Diamond Ring / Protection Ring / Gift For Daughter / Eye Protection Ring / Gift For Her / Womens Stacking Ring / Stackable Bane
![PDF] Multiauthority Traceable Ring Signature Scheme for Smart Grid Based on Blockchain | Semantic Scholar PDF] Multiauthority Traceable Ring Signature Scheme for Smart Grid Based on Blockchain | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/dced8013bbb5878305e2a7440866f8a81bce532b/3-Figure1-1.png)
PDF] Multiauthority Traceable Ring Signature Scheme for Smart Grid Based on Blockchain | Semantic Scholar

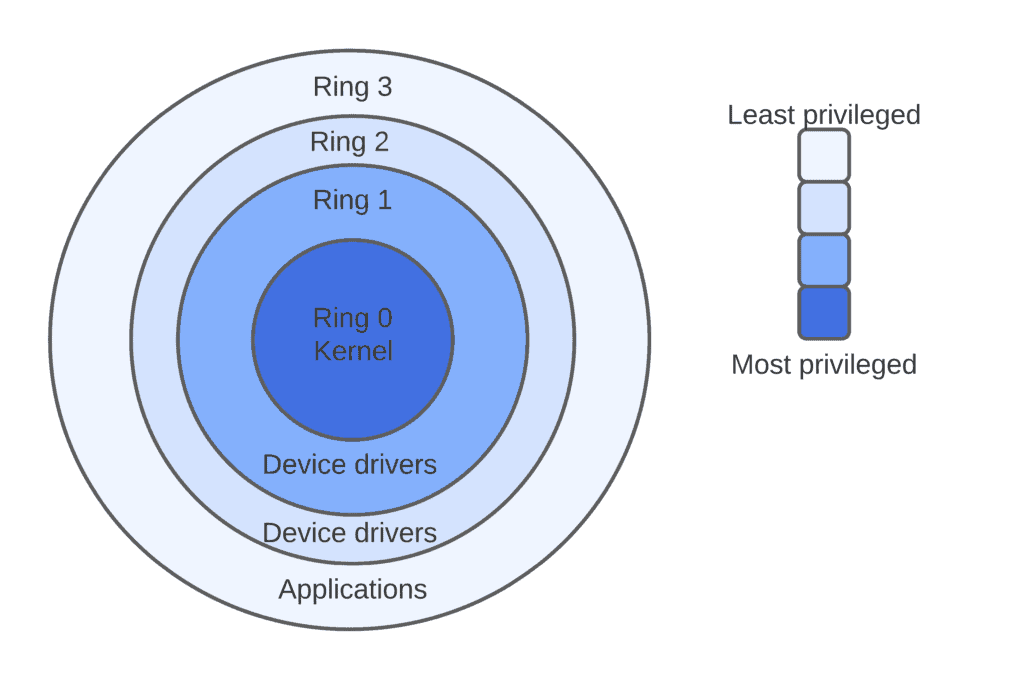
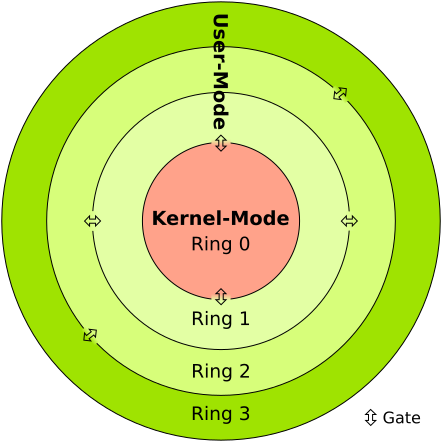
Ch 14 - Chapter 14 - Protection Pages 663-664 Exercises 14.11, 14.14, 14.17, 14.18, 14.20 14.11 - Consider the ring-protection scheme in MULTICS. If we | Course Hero

Figure 4 from Latch-up ring design guidelines to improve electrostatic discharge (ESD) protection scheme efficiency | Semantic Scholar