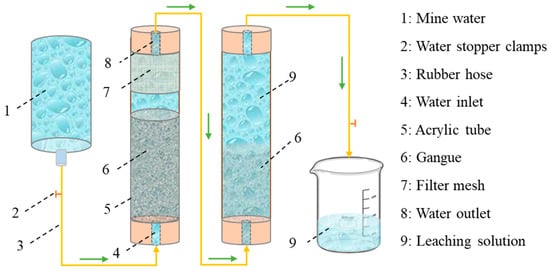
Water | Free Full-Text | Experimental Study on the Purification Mechanism of Mine Water by Coal Gangue

Peter Leimbigler on Twitter: "@austwitnerd @ZachWeiner Conventionally known as rubber-hose cryptanalysis, which is very computationally inexpensive: https://t.co/ZpxKVWWQBh" / Twitter

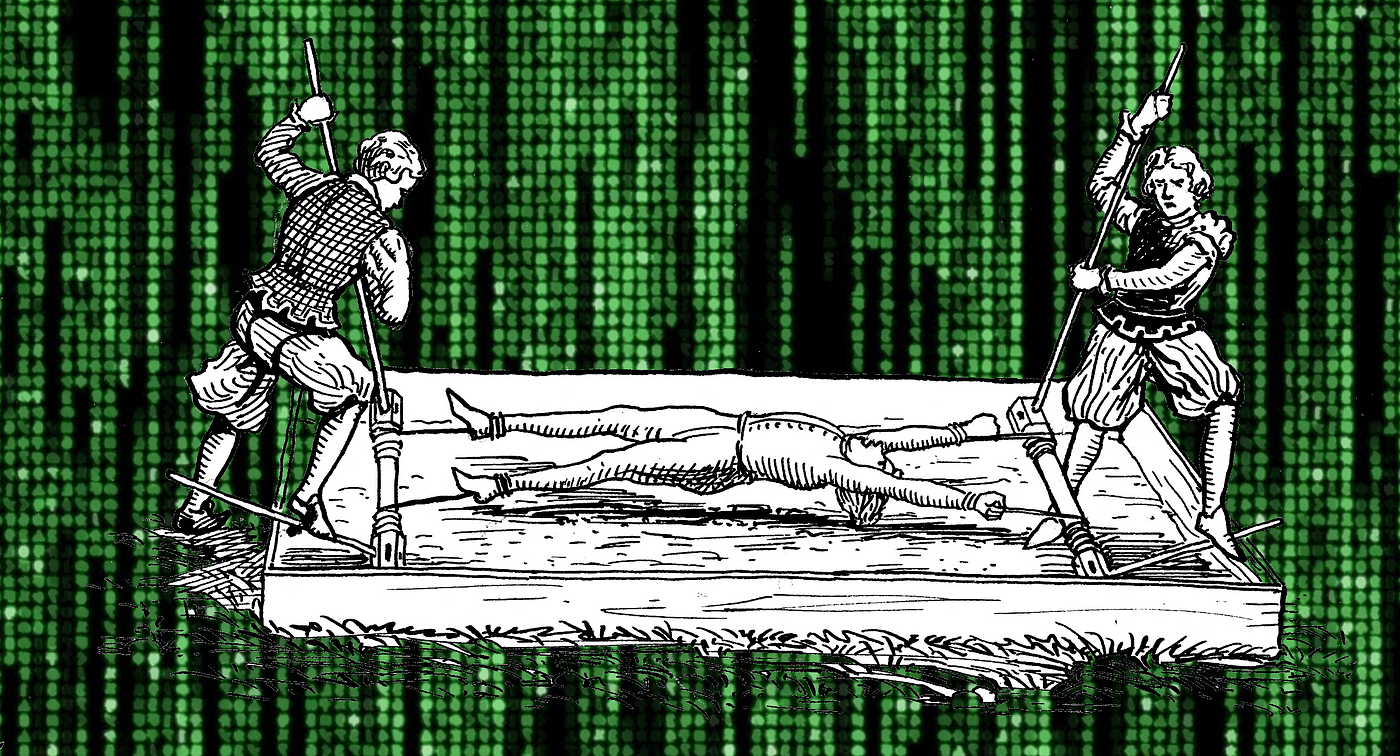
Neuroscience Meets Cryptography: Crypto Primitives Secure Against Rubber Hose Attacks | May 2014 | Communications of the ACM

Amazon.it: Side-Channel Attack: Cryptography, Cryptosystem, Brute Force Attack, Electromagnetic Radiation, Key (Cryptography), History of Cryptography, Cryptanalysis, Rubber-Hose Cryptanalysis - Surhone, Lambert M., Timpledon, Miriam T., Marseken ...

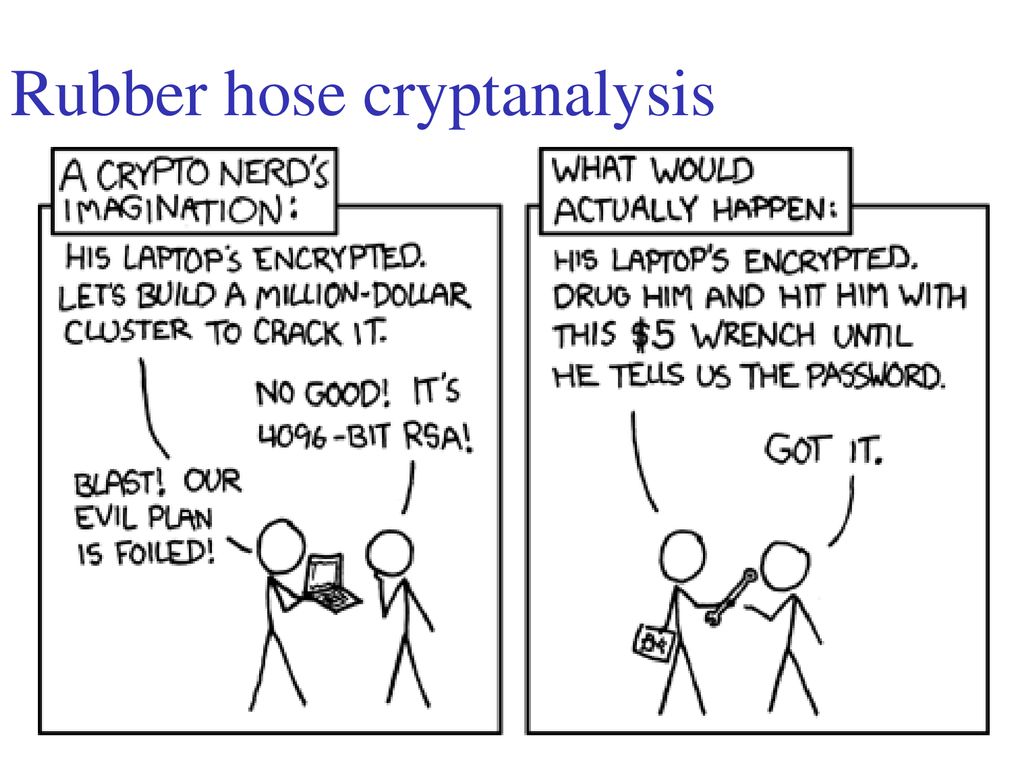
Programmer Humor on Twitter: "Cryptography: expectations vs. reality https://t.co/RD8Tfg057p https://t.co/IpB6X3VFtz" / Twitter

Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks | USENIX

Amazon.co.jp: Rubber-Hose Cryptanalysis : Surhone, Lambert M., Timpledon, Miriam T., Marseken, Susan F.: Japanese Books